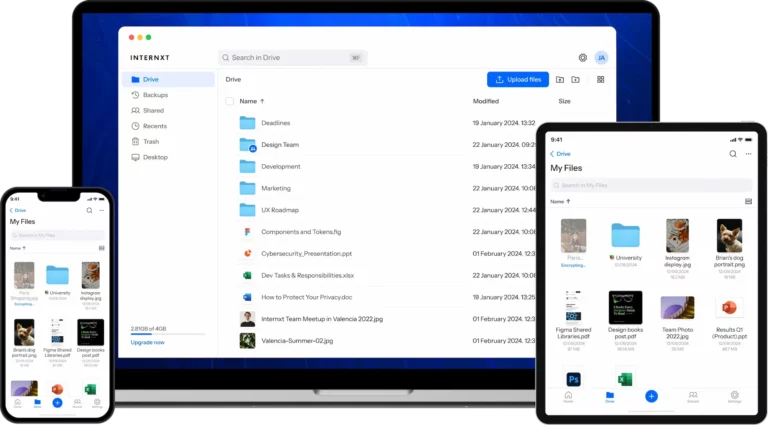
Introducing Internxt Drive: The Private and Secure Cloud Storage Solution
In today’s digital age, where data privacy and security are of paramount importance, Internxt Drive emerges as a game-changer in the cloud storage industry. Developed by Internxt Universal Technologies SL, Internxt Drive is a comprehensive cloud storage solution that prioritizes user privacy and data protection like no other. Let’s delve into the key features and…